User Engagement Analysis

Executive Summary
- Understanding user behavior and engagement is vital for any project/protocol.
- We developed a credit system that analyzes on-chain activity to assess user engagement.
- The system can identify both bad actors and exceptional supporters.
- We deployed this system to assist Gnosis Safe in its airdrop launch.
- In the future, we plan to expand the system's capabilities with our tag library.
Assessing a user's engagement is a fundamental aspect of any project. It provides insights into how people interact with the application and indicates the potential level of retention that can be achieved. It's essential to determine whether users are genuinely interested in your app or if they merely visit it briefly before leaving. When it comes to airdrops, it's crucial to factor in user engagement since you want to ensure that the distribution is fair to reliable participants rather than being taken advantage of by airdrop farmers who sell their rewards as soon as they receive them.
We propose implementing a credit-based system to evaluate users' engagement based on their on-chain activity. Such a system would assess an account's contribution and engagement, among other factors. This approach is particularly useful for airdrops, enabling identifying legitimate supporters of a protocol or project instead of airdrop hunters seeking benefits without contributing. We have used this mechanism successfully to assist Gnosis Safe with token distribution and would like to showcase it as an example of credit-based on-chain data analysis.
Case study: Gnosis Safe
Purpose
The purpose of this project is to ensure a fair distribution of tokens during the upcoming $SAFE airdrop by identifying airdrop farmers beforehand.
Basic idea
To achieve this goal, we propose the implementation of a credit system that can be adjusted by the project team based on their own criteria. This system will allow for flexibility in controlling the level of strictness or leniency when it comes to distributing tokens.
Methodology
In this analysis, we aim to identify suspicious accounts engaged in airdrop farming by analyzing their behavior. To achieve this, we apply the following criteria:
1\ Safe accounts created since 2022/02/10
Safe accounts created after the launch of the $Safe token proposal on February 9th, 2022 (as stated in GIP-29: Spin-off safeDAO and launch SAFE Token). This is because airdrop hunters may be tempted to take advantage of this launch.
2\ Total transaction counts more than 1 but less than 30
Total txn counts between 1 and 30, excluding cases where the interaction time is equal to 1 or greater than 30. Accounts with txn = 1 are considered to be either engaged in real usage (e.g. deposit) or simply a relay app (e.g. calling adding owners function). In contrast, accounts with interaction time > 30 are regarded as highly active accounts with frequent usage.
3\ Short periods of interaction
If all transactions occur within a brief period, such as within a few hours of account setup, it is likely the work of an airdrop farmer. Such activity indicates automated, task-completing behavior designed to obtain drops.
4\ Current token balances of the Safe account are less than 0.02
Safe wallets are multi-sig wallets designed for enhanced asset security. Therefore, we consider a Safe account with balances of all tokens below with little amount (e.g., <0.02 USDC & <0.02 ETH) to be suspicious. Airdrop farmers tend to transfer all their money out of the wallet after completing their interactions. These individuals interact with as many protocols as possible in search of drops, but they leave little money in the wallet. Additionally, in some cases, users may transfer NFTs instead of ERC20 tokens to their Safe accounts. To avoid this happening, we first check if the Safe account has any NFTs.
Simply satisfying one behavior mentioned above can not be considered as robust evidence, whereas satisfying a combination of seven behaviors simultaneously significantly implies the involvement of airdrop farmers.
Results
Certain methodologies, as discussed, were implemented to write queries in Dune to track all the on-chain data that satisfied the specified criteria. All the numeric values were set as parameters, thereby allowing the project side to adjust and finalize the criteria. After the inclusion of all filters, we were able to isolate all the addresses that met the requirements and were flagged as suspicious.
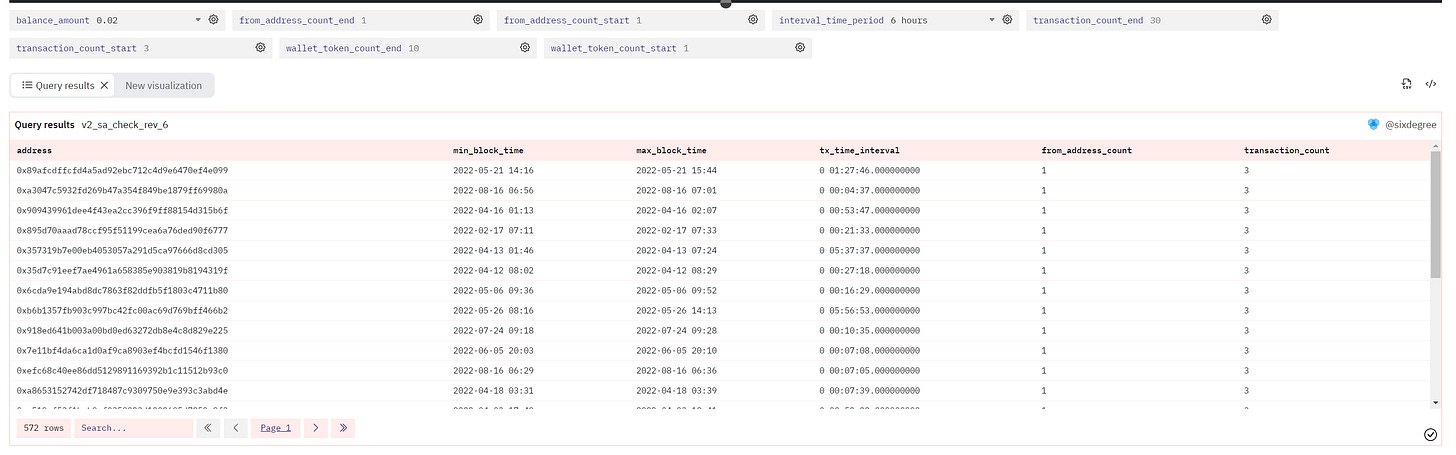
Dune link: https://dune.com/queries/1266525
Please note that this credit system is based solely on the analysis of on-chain activities and is just a prototype. In order to develop a more comprehensive version, we can add more parameters. This system, however, is not only useful for identifying bad actors such as airdrop farmers, but also for recognizing outstanding supporters.
For more details, please check: https://github.com/safe-global/safe-user-allocation-reports/issues/427
zkSync Case
For our zkSync ranking dashboard, we have implemented a modified system with additional features.
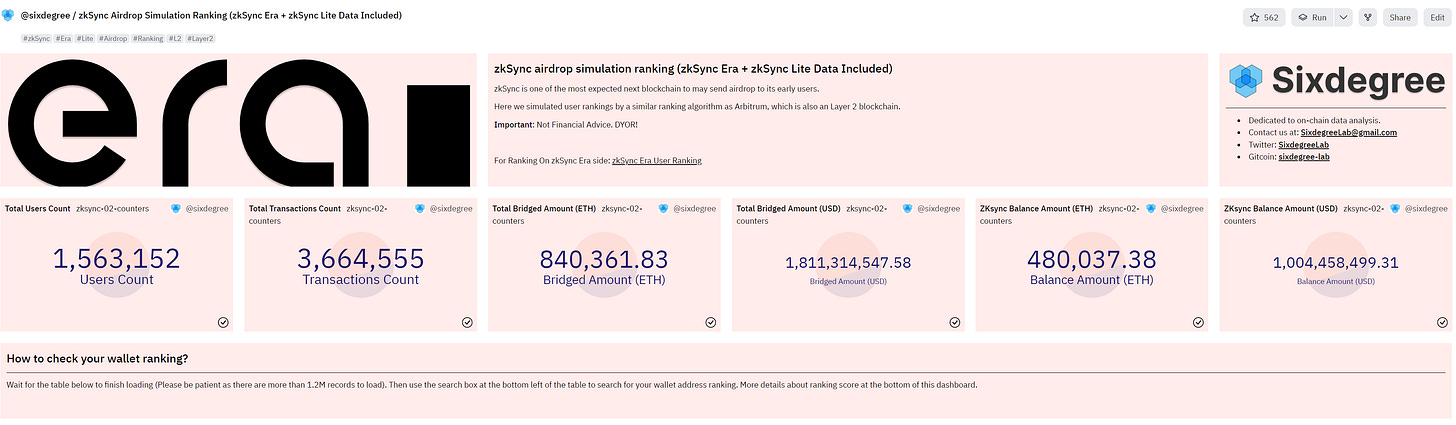
Using Dune, we have created a dashboard that displays bridge information for Ethereum<>zkSync (Lite and Era) and ranks users according to our algorithm.
Dune:zkSync Airdrop Simulation Ranking (zkSync Era + zkSync Lite Data Included)
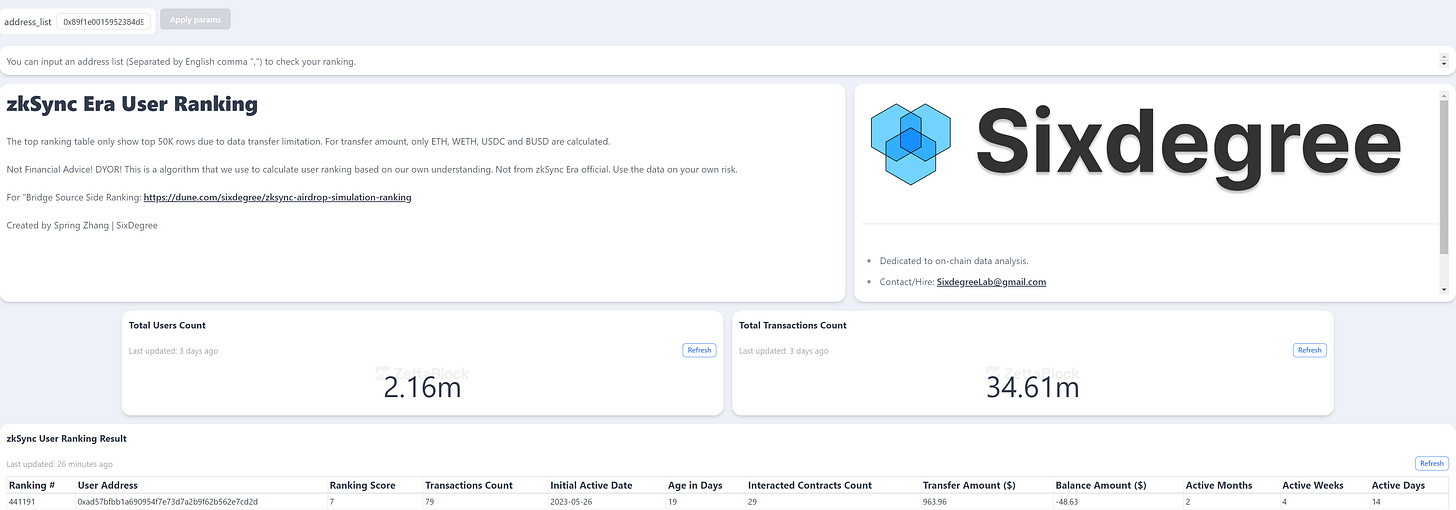
With Zettablock, we've taken this concept one step further by designing a similar ranking dashboard that's solely based on users' behavior on the zkSync Era network. By merging insights from both dashboards, we're able to provide a comprehensive view of user engagement with zkSync.
ZettaBlock - The First Full-stack, Real-time Web3 Data Infra
What's coming next?
In the near future, we will be able to generate more comprehensive and insightful on-chain user profiles through the integration of our tag library. This would enable us to gain a more detailed understanding of each account, their habits, and preferences. For instance, we can differentiate between those who are GameFi enthusiasts and those who are speculative traders. With these enhanced profiles, we can potentially revolutionize the airdrop paradigm and effectively prevent Sybil attacks from their very foundation.
How can we collaborate?
We are looking to partner with top protocols and would love to discuss your data needs! Feel free to contact us!
- Email: [email protected]
- Twitter: https://twitter.com/SixdegreeLab
- Telegram: https://t.me/oxgummy